iMessage PQ3
Earlier this year, we announced iMessage PQ3, Apple’s formally-verified protocol for end-to-end encryption that amongst other updates provides post-quantum protections against “Harvest Now, Decrypt Later” attackers.
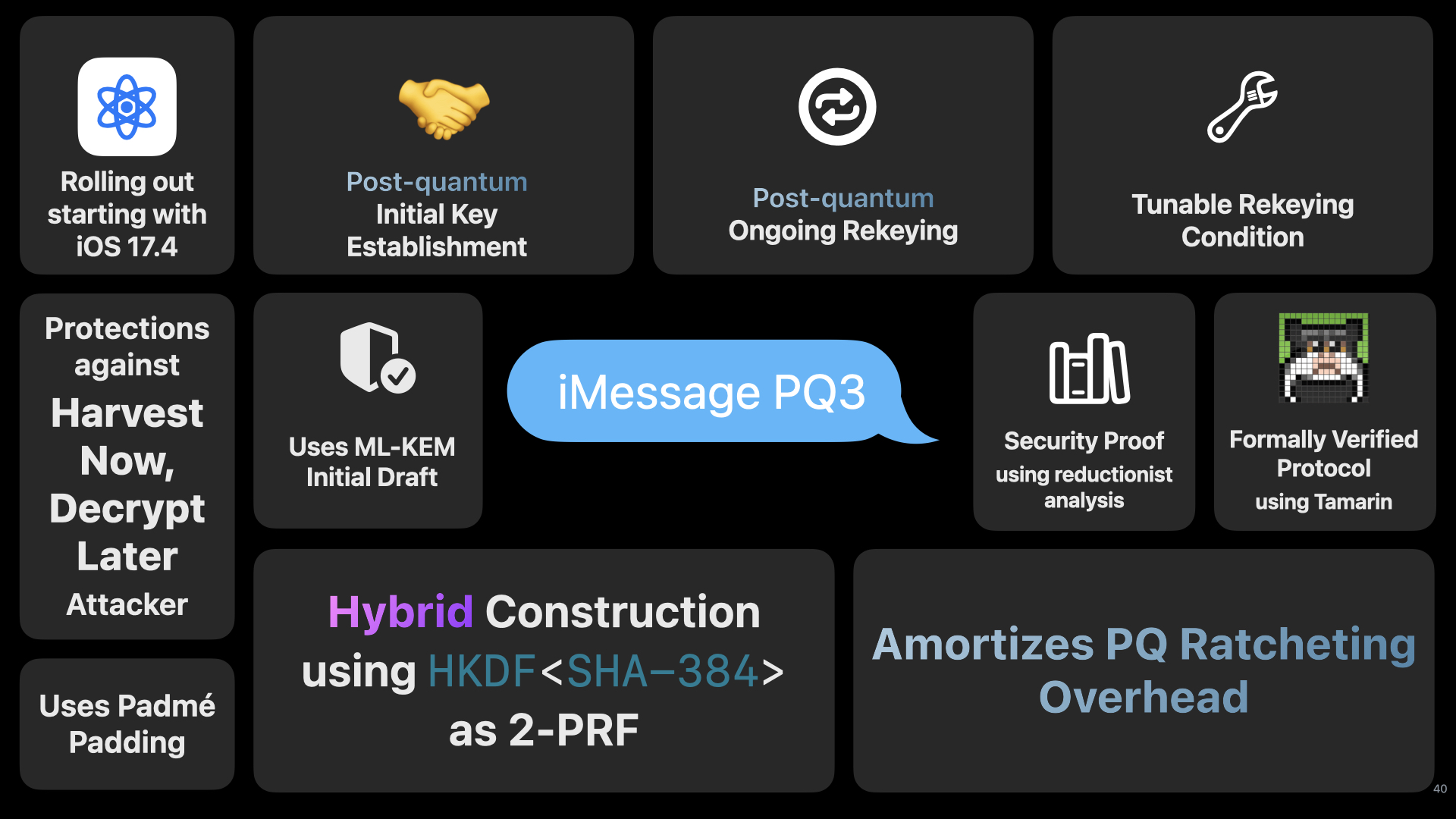
In a previous blog entry, I talked about the Double Ratchet & the Quantum Computers, concluding that Double Ratchet was ‘Quantum Annoying’ and required an attacker to record almost every message to be able to continue decrypt a conversation due to the key continuity property of the public-key ratchet. Post-quantum ratcheting; however, still required some tricks to be practical in order to not trade post-compromise security for quantum-resistance.
In the Real World Crypto 2024 Invited Talk: Designing iMessage PQ3: Quantum-Secure Messaging at Scale, we cover the design of the iMessage PQ3 protocol, including the delicate balancing act between crytographic overhead from larger post-quantum parameters and tightness of security properties.